In today’s digital world, where things change quickly, network security is very important for both people and businesses. The word “Network Access Control (NAC)” has become very important in the ongoing fight to keep networks safe from threats and people who shouldn’t be able to get in. The first line of defense against unauthorized users, devices, and possible holes in a network infrastructure is NAC, which is a comprehensive security solution.
This study goes into detail about the main ideas of Network Access Control (NAC), looking at what it is, how it works, and how it can help make networks safer. We’ll talk about how NAC works as a watchdog, making sure that only trusted and compliant devices can access sensitive data. This makes it an important part of cybersecurity.
What does NAC (Network Access Control) mean?
It is not just software or technology; it is a complete way of doing things that lets companies enforce rules and policies about who can join a network. Network Access Control (NAC) helps keep your network safe by regularly checking the identity, security, and compliance of devices and users that want to join. It does this by checking their identity, security posture, and compliance.
The Importance of Network Access Control (NAC)
In this digital age where keeping private data safe is becoming more and more important, the word “Network Access Control (NAC)” has become very important in the field of cybersecurity. But what does Network Access Control (NAC) really mean? NAC isn’t just a technology; it’s a whole security strategy meant to keep networks safe from risks and people who shouldn’t be there. NAC works as a watchdog, making sure that only trusted and legal entities are allowed access by regularly checking the identity, security compliance, and overall health of devices and users trying to connect to the network. We will talk about the main ideas behind Network Access Control (NAC), how important it is in current cybersecurity strategies, and how it is the most important thing that can be done to make networks safer.
Types of Network Access Control
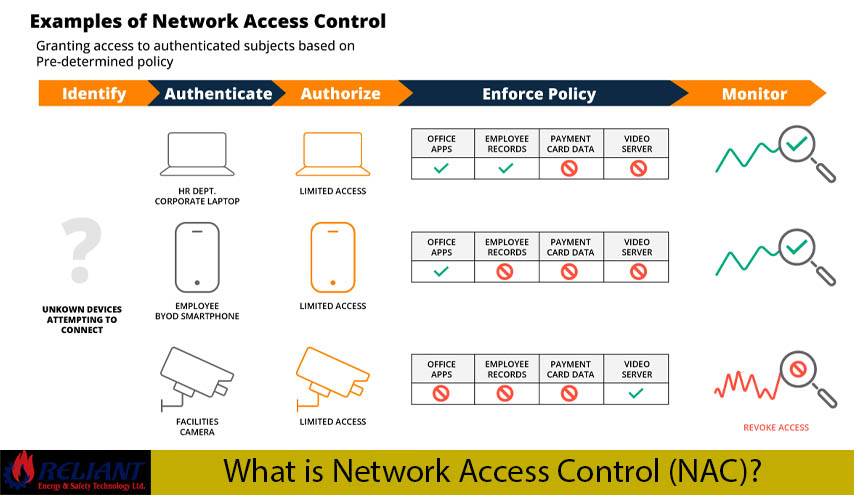
Network Access Control, or NAC, includes a lot of different types and methods, and each one manages and protects network access in its own way. The following are some popular types of NAC:
Pre-connect NAC: Pre-connect NAC checks access rules and makes sure they are followed before a device connects to the network. It checks that a device meets certain security standards and checks that it does so before letting it in.
Post-connect NAC: This type of NAC checks devices for compliance after they’ve linked to the network and is watching what they do. If a device is found to be not following the rules, the right steps are taken, like putting it in a quarantine or limiting its access.
802.1X NAC: The IEEE 802.1X standard is used for network access control in this method. It uses authentication methods like EAP (Extensible Authentication Protocol) to make sure that only approved devices and users can connect to Wi-Fi networks.
Agent-Based NAC: Software agents need to be installed on endpoint devices for agent-based NAC systems to work. These workers help make sure that security policies are always being followed, evaluated, and monitored.
Agentless NAC: This method doesn’t need software to be installed on host devices like agent-based NAC does. It uses network-based checks and scans to make sure it’s compliant and manages access.
Mobile NAC: This type of NAC is designed to work with smartphones and tablets by enforcing rules and managing access. It deals with the special problems that come up with protecting mobile devices.
Cloud NAC: NAC systems that run in the cloud are scalable and can be managed from one place. They work well for businesses with workers who are spread out or who work from home.
Different types of NAC are used to protect different types of networks, and companies usually pick the method that works best with their infrastructure, security goals, and legal needs.
How to choose a network access control product
It is very important to choose the right Network Access Control (NAC) tool if you want to make your network safer. Key things should be thought about to make the best choice. First, you should look at how big, complicated, and detailed your network’s needs are, including any compliance standards. Make sure that the NAC product meets these needs. It is very important that it can be integrated with your current network system. To allow for future growth, scalability is important. You should also think about the different kinds of people and gadgets that are connecting to your network. By carefully looking at these things, you can pick a NAC solution that meets the security and operational needs of your business the best.
What Are the Benefits of NAC?
Network Access Control (NAC) is one of the most important parts of keeping modern networks safe and secure. Here are the top five reasons why NAC offers significant benefits:
Better security: NAC acts as a guard, making sure that only devices and users that are allowed to and follow the rules can connect to the network. This makes the chance of hackers, data breaches, and unauthorized access much lower. NAC is a watchful guardian that keeps sensitive data and network resources safe by enforcing security policies.
Compliance Assurance: NAC solutions help businesses follow the rules and policies that govern their own security. NAC lowers the chance of fines and data breaches related to noncompliance by making sure that all connected devices meet certain compliance standards.
Better Network Visibility: NAC lets you see all of the devices on your network at once. This better visibility makes it easier to keep an eye on, manage, and respond to possible security threats. Network administrators can quickly find strange or suspicious behavior and stop it.
Reduced Attack Surface: NAC reduces the attack surface by keeping devices that aren’t supposed to be there from getting on the network. By doing this, it greatly lowers the number of possible entry points for cyber threats, making the network safer overall.
Quick Response to Threats: NAC can handle security threats on its own. It can quarantine devices that don’t follow the rules or that look fishy, preventing them from connecting to the network until the problem is fixed. This quick response helps keep threats from doing too much damage and keeps network security strong.
Network Access Control has many advantages, such as better security, assurance of compliance, better network visibility, a smaller attack surface, and quick response to threats. NAC is an important part of overall network security plans because it has these benefits that are necessary in the ongoing fight against cyber threats.